Phishing Security
Cyber-attacks can happen in any business, in any country and in any industry. Perpetrators are getting more creative and patient while searching for unsuspecting victims. Phishing (sounds like fishing) security scams are attempts to trick individuals or organizations into giving out personal or confidential information. This could include bank account numbers, addresses, passwords or other. It could also be requests to pay bills, or gain access to your internal network.
Types of Phishing
There are three forms of Phishing that can affect business: Phishing, Spear Phishing and Whaling. These attacks vary in nature, but no different in how they put your business, data and your employees at risk. Malicious attacks of this nature tend to be directed from an email to what is known as a phishing website that looks and feels very similar to the real company they are be imitating.
- Phishing, in general, are mass produced communication pieces made by perpetrators and sent to the public. They mimic trusted sources (Amazon, Netflix, PayPal, bank, government body etc) and send a form of communication that looks legitimate. Delivery of such attacks include email, text or instant messages (Facebook, Instagram, forums or other).
- Spear Phishing is a more sophisticated and targeted. Attackers focus on mid-level employees, and more often a department or group within the organization to gain confidential information by posing as upper level managers or other businesses, for example. This could be in the form of a invoice to be paid, or offer of services.
- Whaling, think big “fish”, is similar to spear phishing but targets high-level executives like CEO’s and CFO’s. Scammers can find quite a bit of information regarding these key personnel, including looking online through searches, social media platforms and websites. Perpetrators will use this information to send more detailed scams to unsuspecting victims.
Phishing Examples
When opening personal or business emails it is important to know what to look for to avoid being a victim of phishing. Phishing emails will pretend to be large organizations such as Netflix or your national government agency. The typical method of operation is to request payment by stating payment has failed. Or the email will be regarding forgotten passwords, or updating information. There are many clever ways for perpetrators to request information and these examples are not inclusive. The emails are what is called “spoofed” and look and feel legitimate. Thus making it more difficult to spot. Perpetrators may use logos, security features and other details that would have victims believe it is real communication.
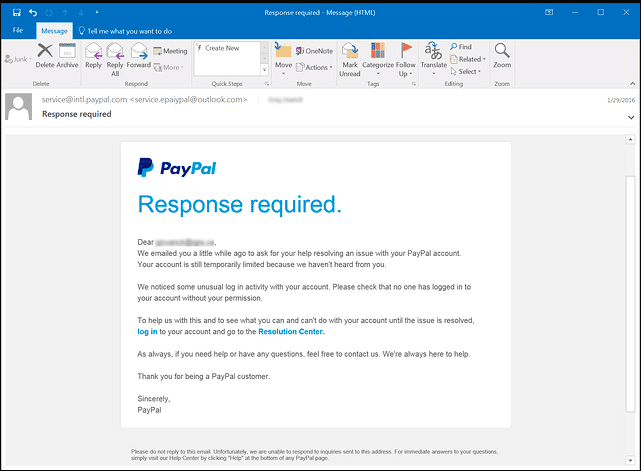
In this example, it is very difficult to notice that it is in fact a phishing email. The grammar is poor and you may spot a letter missing in the return email address.
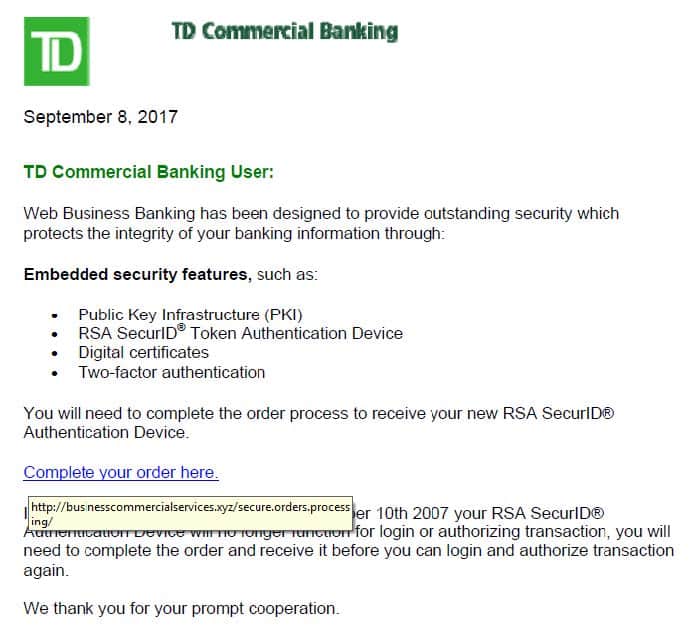
Here, you can see there is a link in the body of the email. The logo and wording looks legitimate. However, the link when hovered over goes somewhere completely different.
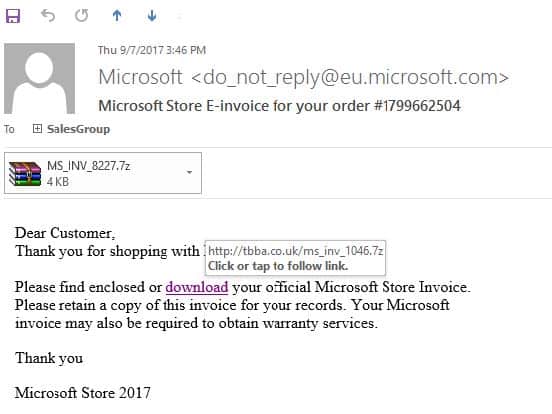
Here you can see there is what appears to be an attachment AND a link. Hovering over it will show that it is in fact NOT a legitimate link.
To see more examples, visit Phishing Org: Phishing Examples
HTTPS – What it is and why it matters
Websites with addresses that start with “https” are supposed to provide privacy and security to visitors. After all, the “s” stands for “secure” in HTTPS: Hypertext Transfer Protocol Secure. In fact, cyber security training has focused on encouraging people to look for the lock icon that appears in the web address bar on these secure sites. The presence of “https” and the lock icon are supposed to indicate the web traffic is encrypted and that visitors can share data safely.
Unfortunately, cyber criminals are relying on the public’s trust of “https” and the lock icon. They are more frequently incorporating website certificates—third-party verification that a site is secure—when they send potential victims emails that imitate trustworthy companies or email contacts. These phishing schemes are used to acquire sensitive logins or other information by luring them to a malicious website that looks secure.
The lock icon did carry more weight years ago, when getting an SSL/TLS certificate was a more difficult process, but these certificates are now free and can be acquired by anyone. Attackers are increasingly making sure that their phishing sites have authentic certificates to mimic legitimate websites.
If you are not careful, you can become victim of a phishing scam. It can be easy to open your email inbox and notice something that looks familiar, but not quite. Yet you may not think anything of it because you shop at that retail store, or bank with that bank, or any other reason. That is exactly what scammers are hoping.
Protecting your business from Phishing:
Educate your employees on Phishing to minimize attack opportunities. It is good practice to educate and train team members on what phishing. Knowing the basics, but also being diligent in looking at emails thoroughly will help diminish the likelihood of falling victim. Download our Ransomware Cheat Sheet for quick reference and to share with staff.
The following steps can help reduce the likelihood of falling victim to phishing:
- Do not simply trust the name on an email: question the intent of the email content. Hover over any links within the email (notice where it wants to be direct to)
- If you receive a suspicious email with a link from a known contact, confirm the email is legitimate by calling or emailing the contact; do not reply directly to a suspicious email.
- Check for misspellings or wrong domains within a link (e.g., if an address that should end in “.gov” ends in “.com” instead).
- Do not trust a website just because it has a lock icon or “https” in the browser address bar.
This type of diligence may add a few minutes to your day, but it is trivial compared to the damage that can be caused by falling for a phishing attack. New-age security awareness training can build a culture of security within your organization, so that your employees will recognize potential red flags out of habit.
A Managed IT Services company can help minimize cyber-attack risks
To minimize phishing attempts, outsourcing a credible Managed IT Services company to maintain and monitor your systems is good business. They can help with all forms of security, including email, two-step verification and more.
In the event of an attack, any business can lose thousands up into the millions of dollars. The investment for security is minimal in comparison to what the potential downfall could be. Consider it to be insurance – and also get cyber insurance – to know your business is safe in the event of an attack.
There is no real way to prevent perpetrators from sending phishing emails, but there are ways to mitigate them from getting into inboxes and to learn how to spot them and delete them immediately.
Contact us today to learn more about how we can help your business to reduce cyber-attack risks.

